Roles and Permissions Management
This document outlines the roles and permissions for users within the Automox console. It defines default user roles, their associated permissions, and guidelines for creating custom user roles. The aim is to ensure that users have appropriate access levels to perform their tasks efficiently while maintaining system security and integrity.
Automox includes two main administrative roles with global permissions across all organizations in an account: account administrator and full administrator. The account administrator manages account-related details such as billing, user and role management, and creating or deleting organizations. The full administrator manages operational functions across organizations, including devices, groups, policies, remediations, reports, and API keys.
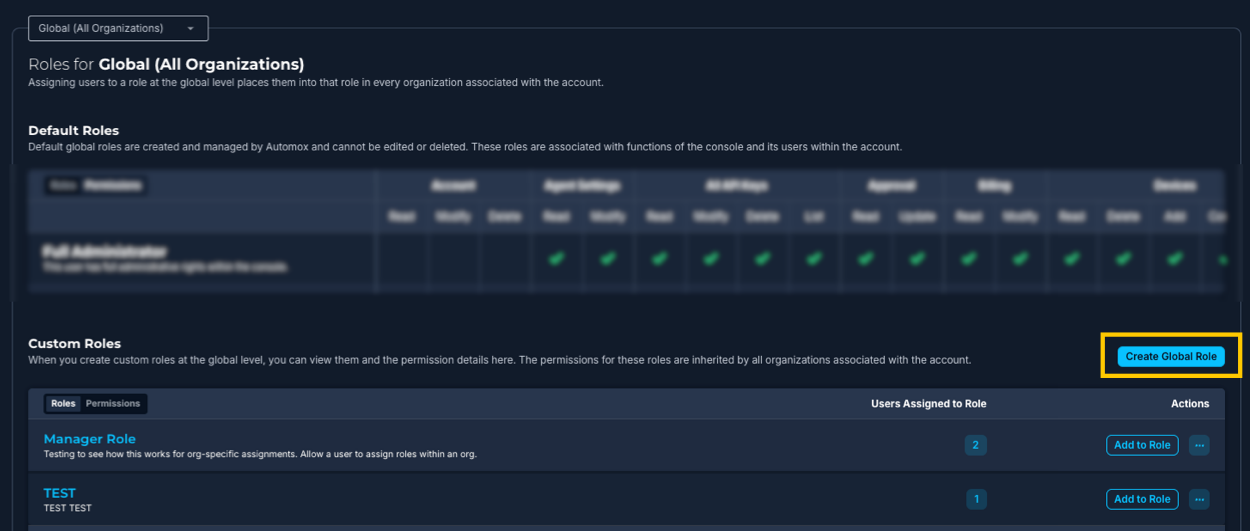
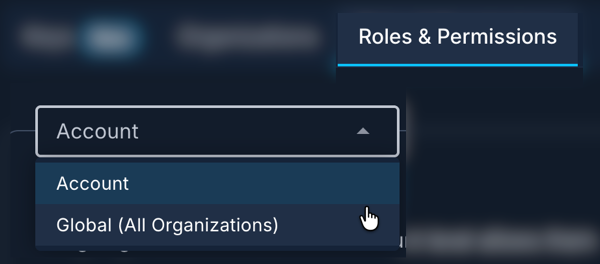
From the Roles and Permissions page, you can select either Account to view details for the account administrator, or Global (All Organizations) to view details for the full administrator and other global roles.
- Access to the Roles and Permissions tab in the console is managed through RBAC Roles permissions.
- You can view the tab with RBAC Roles: Read permissions, or you can manage it if you are, for example, a Global Full Administrator.
- See Default User Roles and Permissions.
API keys inherit the same permissions that the user has. For example, an API key belonging to a full administrator has the same permissions as in the console, and allows them to perform functions using the API that require full administrator permissions.
An API key belonging to an organization operator is only able to access and view organizations where they are assigned organization operator permissions using the API.
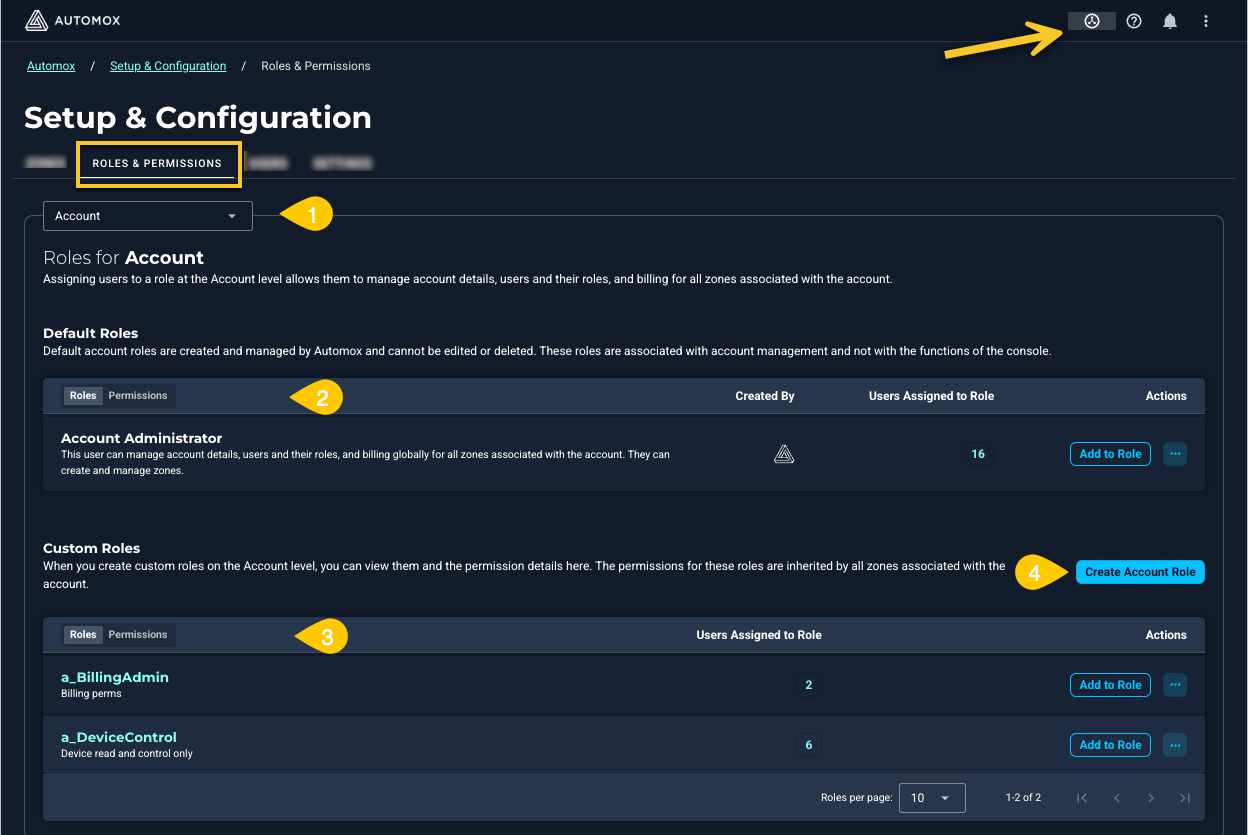
About the Roles and Permissions Page
From the Manage Orgs and Users (Global View) menu in the console, select Setup & Configuration → Roles and Permissions.
This page allows you to manage and create user roles with precise permissions for your organization's needs.
Options available:
- Role association: Account or Global (All Organizations)
- List of roles: View, duplicate, and add or remove users from roles
- List of permissions: View permissions available to each role. Scroll to view the full list.
- Custom role creation: Assign specific permissions for tailored use.
Default User Roles and Permissions
This section describes the pre-defined (default) roles and their permissions. From the Roles and Permissions tab, select the role level that you want to view details for: Account or Global (All Organizations).
- Default roles cannot be modified.
- Some features require additional role and permission combinations. See Feature-Specific Access Requirements for details.
1. Account Administrator
Description: Account administrators manage account details, users and their roles, and billing globally for all organizations associated with the account. They can create and manage organizations. Only account administrators can add (invite) users to an account or assign roles at the account level.
| Function | Permissions |
|---|---|
| Account | Read, Modify, Delete |
| Billing | Read, Modify |
| Organization | Read, Create, Manage |
| Personal API Keys | Manage |
| RBAC Roles | Read, Modify, Delete, Create, Grant, Revoke |
| Users | Read, Modify, Delete, Invite |
2. Full Administrator
Description: Full administrators have global permissions for operational management across all organizations in the account. They can manage devices, groups, policies, remediations, reports, and API keys, and can create and manage custom roles that fall under the Global (All Organizations) role type.
A full administrator can be assigned globally from the Roles and Permissions page or at the organization level from Settings → Users. When assigned at the organization level, the same operational permissions apply, but only within that organization.
| Function | Permissions |
|---|---|
| Agent Settings | Read, Modify |
| All API Keys | Read, Modify, Delete, List |
| Approval | Read, Update |
| Billing | Read, Modify |
| Devices | Read, Delete, Add, Control, Manage |
| Groups | Read, Modify, Delete, Create |
| Organization | Read, Manage |
| Package | Read, Manage |
| Patch Policy | Read, Modify, Delete, Create, Execute |
| Personal API Keys | Manage |
| Queries | Read, Manage |
| Remediation | Read, Modify, Delete, Create, Execute |
| Remote Control Consent | Manage |
| Reports | Read |
| Required Software Policy | Read, Modify, Delete, Create, Execute |
| RBAC Roles | Read, Modify, Delete, Create, Grant, Revoke |
| SAML | Read, Manage |
| Scheduled Windows | Read, Modify, Delete, Create |
| Software | Read |
| 2FA (Two-factor authentication) | Read, Modify, Delete, Create |
| Users | Read, Modify, Delete, Invite |
| Worklets | Read, Modify, Delete, Create, Execute |
3. Organization Operator
Description: Organization operators have full administrative rights for policies, groups, and devices in a specific organization. They can also conduct remote control sessions.
| Function | Permissions |
|---|---|
| Agent Settings | Read |
| Approval | Read, Update |
| Devices | Read, Delete, Add, Control, Manage |
| Groups | Read, Modify, Delete, Create |
| Organization | Read |
| Package | Read, Manage |
| Patch Policy | Read, Modify, Delete, Create, Execute |
| Personal API Keys | Manage |
| Queries | Read, Manage |
| Remediation | Read, Modify, Delete, Create, Execute |
| Reports | Read |
| Required Software Policy | Read, Modify, Delete, Create, Execute |
| RBAC Roles | Read |
| SAML | Read |
| Scheduled Windows | Read, Modify, Delete, Create |
| Software | Read |
| Worklets | Read, Modify, Delete, Create, Execute |
4. Patch Operator
Description: Patch operators can create, modify, and delete patch policies, read and run (execute) worklets and required software policies, and read, but not manage devices
| Function | Permissions |
|---|---|
| Agent Settings | Read |
| Devices | Read |
| Groups | Read, Modify |
| Organization | Read |
| Package | Read |
| Patch Policy | Read, Modify, Delete, Create, Execute |
| Personal API Keys | Manage |
| Queries | Read |
| Remediation | Read |
| Reports | Read |
| Required Software Policy | Read, Execute |
| RBAC Roles | Read |
| SAML | Read |
| Scheduled Windows | Read |
| Software | Read |
| Worklets | Read, Execute |
5. Helpdesk Operator
Description: Helpdesk operators have full read rights within a specific organization. They can also conduct remote control sessions.
| Function | Permissions |
|---|---|
| Agent Settings | Read |
| Devices | Read, Control |
| Groups | Read |
| Organization | Read |
| Package | Read |
| Patch Policy | Read |
| Personal API Keys | Manage |
| Queries | Read |
| Reports | Read |
| Required Software Policy | Read |
| RBAC Roles | Read |
| SAML | Read |
| Scheduled Windows | Read |
| Software | Read |
| Worklets | Read |
6. Billing Administrator
Description: Billing administrators have full read rights and can read and modify billing information and subscriptions.
| Function | Permissions |
|---|---|
| Billing | Read, Modify |
| Devices | Read |
| Groups | Read |
| Organization | Read |
| Package | Read |
| Patch Policy | Read |
| Personal API Keys | Manage |
| Queries | Read |
| Reports | Read |
| Required Software Policy | Read |
| RBAC Roles | Read |
| SAML | Read |
| Scheduled Windows | Read |
| Software | Read |
| Users | Read |
| Worklets | Read |
7. Read Only
Description: Users with this role can read all content within a organization.
| Function | Permissions |
|---|---|
| Agent Settings | Read |
| Billing | Read |
| Devices | Read |
| Groups | Read |
| Organization | Read |
| Package | Read |
| Patch Policy | Read |
| Personal API Keys | Manage |
| Queries | Read |
| Remediation | Read |
| Reports | Read |
| Required Software Policy | Read |
| RBAC Roles | Read |
| SAML | Read |
| Scheduled Windows | Read |
| Software | Read |
| 2FA | Read |
| Users | Read |
| Worklets | Read |
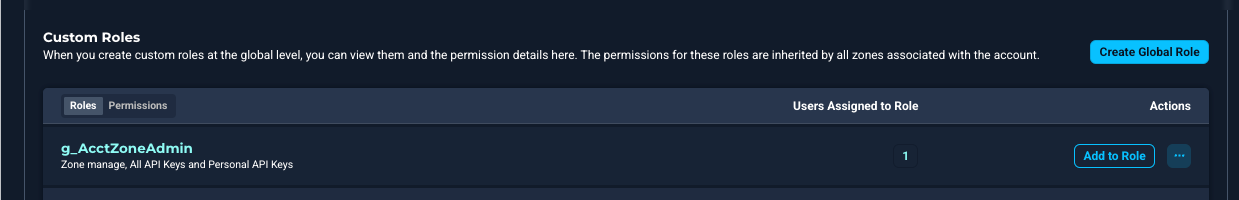
Custom User Roles
Administrators and users with the required RBAC Roles permissions can create, delete, and assign custom roles with tailored permissions.
- Account-Level Custom Roles: To create or delete roles at the account level, you must have account-level permissions. These roles are not visible at the global or organization level.
- Global-Level Custom Roles: To create or delete roles at the global level, you must have global-level permissions. Global-level roles are inherited by all organizations associated with the account.
Refer to Guidelines for Single Organization RBAC Management if you are considering expanding your account.
Creating a Custom User Role
You can create a custom user role from the Custom Roles section of the Account or Global (All Organizations) page.
- Custom roles have no restrictions or safeguards, so be mindful of dependencies when assigning permissions. For example, a role managing devices must also include the ability to read device information to function properly. Always review permissions to ensure the role works as intended.
- For feature-level requirements that are not shown in the permissions tables, see Feature-Specific Access Requirements.
- You can now delete a custom role from the list of custom roles. Deleting a role is permanent and cannot be reversed. See Deleting a Custom User Role
- Choose a role association:
- Choose whether the new role has Account or Global (All Organizations) permissions.
- Note: Roles assigned within the Setup & Configuration → Roles and Permissions page are then available across all organizations.
- Select the create button:
- If you selected Account in the previous step, go to Custom Roles and select Create Account Role.
- If you selected Global (All Organizations) in the previous step, go to Custom Roles and select Create Global Role.
- Note: The available permissions differ between account and global roles.
- Define Role Name and Description:
- Enter a unique name for the role.
- Write a brief description to explain the role’s purpose.
- Select Base Permissions:
- Start with a set of base permissions similar to existing roles (for example, Patch Operator or Helpdesk Operator).
- Note: You can also duplicate an existing role or custom role, and modify its permissions as needed.
- Customize Permissions:
- Add or remove specific permissions as needed. Permissions can include:
- Read, Modify, Delete, Create permissions for different data types (for example: remediation, patch policies, RBAC)
- Ability to manage specific settings such as manual approval, or remote control consent
- Add or remove specific permissions as needed. Permissions can include:
- Assign Role to Users:
- Assign the custom role to one or more users.
- Note: You can assign multiple roles to users simultaneously.
Deleting a Custom User Role
You can delete a custom user role from the Custom Roles section of the Account or Global (All Organizations) page. You must have the corresponding required permissions to delete global and account-level custom roles.
- Locate the custom role you want to delete.
- Under Actions, select Delete Role.
- In the confirmation dialog, review the details and confirm that you want to delete the role.
Deleting a role is permanent and cannot be undone.
- All users are removed from the deleted role.
- If a user assigned to this role has another role assigned, only this role is removed and the other assignment remains.
- If a user is only assigned to this role, deleting it leaves them unassigned to any role.
- If you do not have the required permissions, the Delete Role option is disabled.
- Automox Default Roles cannot be deleted.
Notification Tray
You can see the progress of these updates in the notification tray of your console.
Legend
The legend is available when you are creating or editing a custom role. This explains permissions for each function. Use it as a reference when creating custom roles to ensure proper access control.
- Add: Permits appending new items or data to existing sets or collections.
- Control: Provides the ability to initiate a remote control session.
- Create: Allows the generation or addition of new information or data.
- Delete: Provides the ability to remove information or data.
- Execute: Allows performing or carrying out specific tasks or operations.
- Grant: Allows you to add users to default and custom roles.
- Invite: Allows the capability to invite others to join or participate in the console.
- Manage: Enables comprehensive control, including configuring settings and overseeing operations.
- Modify: Permits changing or editing existing information or data.
- Read: Allows viewing and accessing information or data.
- Revoke: Allows you to remove users from default and custom roles.
- Update: Allows the user to approve or reject a patch.
Custom Roles Table
From the custom roles table, you can view the list of all roles that have been created and their permissions.
| Table Option | Description |
|---|---|
| Roles / Permissions |
|
| Users Assigned to Role | This shows the number of users assigned this role. Click to open a list of assigned users. |
| Add to Roles | Click to add users to this role. |
| Actions |
|
Viewing a Custom Role
Click the name of the custom role to view the details of the role. On the details page, you can edit the information or permissions, create a duplicate, or add or remove user assignments.
- Save any changes or to exit this page, click Back.
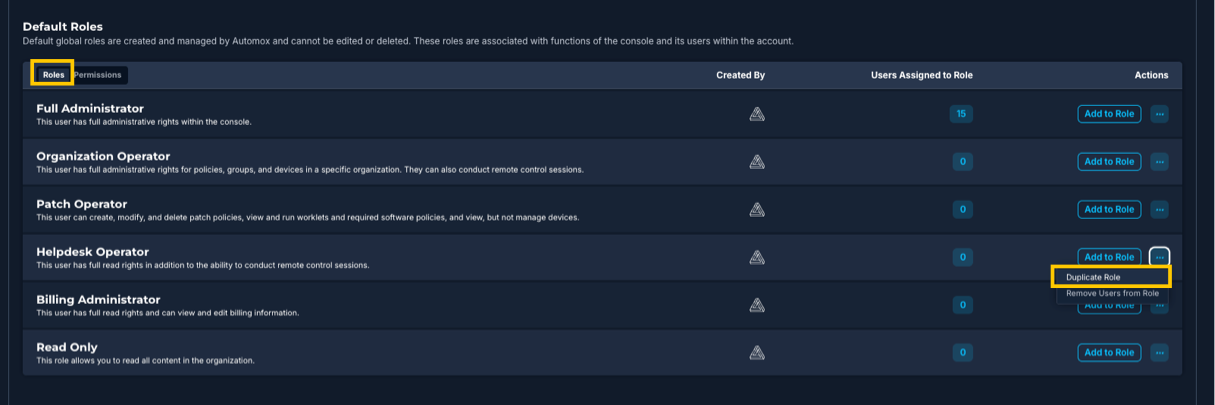
Duplicating a Role
To simplify creating a new role, you can create a copy of an existing default or custom role and modify it as needed.
- From the Roles tab, find the role you want to use as a basis for a new custom role.
- Under Actions, click Duplicate Role. This creates a copy of the role on the custom role page.
- Edit the Custom Name and provide a description for the new role.
- Make any adjustments to the permissions. (Ensure this is what you want before saving.)
- Save and assign any users to the new role.
Assigning Users to a Role
You can add users to an existing role or a new role at the time of creating a custom role.
- To add users to a role, select Add to Role for the corresponding role.
- In the Add Users to Role window, select the email address for each user you want to assign the role to.
- Click Add User.
A notification appears in the console to confirm the status of the added role. - You can view the assigned users by clicking on the number in the Users Assigned to Role column.
Note: Roles assigned within the Setup & Configuration → Roles and Permissions page are then available across all organizations.
Example: When you assign the role Help Operator to a user from the global Roles and Permissions page, they appear as a Help Operator throughout all organizations related to the account.
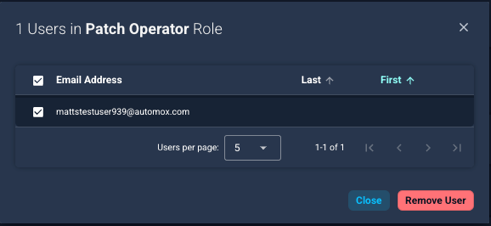
Removing Users from a Role
You can remove users from a role at any time.
- You must have at least one user in the Full Administrator role at all times. If you want to remove a user from that role, you must assign the Full Administrator role to another user.
- A user can be removed from all roles. If the user is removed and does not have a role assignment, they are still visible in the Users table and can be edited and added to a role by anyone with the required permissions. When the user logs into the console, a message appears that informs them to contact their administrator to be assigned a role.
There are two ways to remove users from a role:
- Select Actions → Remove Users from Role.
- In the Remove Users from Role dialog window, select the email address of each user you want to remove from the role.
- Click Remove User.
- Confirm the removal.
You can also start from the Users Assigned to Role column.
- Click the number in the Users Assigned to Role column.
- In the dialog window, select the email address of each user you want to remove from the role.
- Click Remove User.
- A notification appears in the console to confirm the status of the revoked role.
Example Custom User Roles
1. Global Worklet Manager
Description: This Global Worklet Manager has full permissions associated with Worklets and can read reports. Permissions:
- Read, modify, delete, create, and execute worklets
- Read reports
2. Device Administrator
Description: Device administrators can manage all aspects of managing devices for the organization they are assigned to. Permissions:
- Read all device information.
- Add, delete, and manage devices
- Use remote control to manage devices remotely
3. HR Manager
Description: HR Managers handle user management and administrative tasks related to employee data. Permissions:
- Read, modify user accounts
- Manage user roles and permissions
- Limited access to billing and subscription details
Dependency Mapping
The following table are examples of some of the dependencies that should be taken into account when creating custom roles. Refer to Default User Roles and Permissions.
| Function | Dependency: These permissions should be assigned together |
|---|---|
| Remote control consent requires the ability to read devices. |
|
| To add a device requires the access key. You need permission to view the organization. |
|
| A policy manager might require group read permissions to be able to associate the policies they create to groups. |
|
| A role with RBAC permissions also requires organization and user read permissions. |
|
| A role that can modify a user account requires other RBAC permissions. To be able to assign roles you need the following: |
|
| Billing administrators need the permission to read within the organization. |
|
| Group management (adding or editing groups) requires the ability to read devices. |
|
| A role with permissions to read reports also requires the permission to read the organization. |
|
Feature-Specific Access Requirements
Some features in Automox require a combination of roles and permissions beyond what is shown in the standard permissions tables. The following table lists common examples.
Access within organizations
Roles assigned at the organization level apply only to devices within that organization.
| Feature | Dependency: These roles or permissions are required |
|---|---|
| Ask Otto |
|
| Script Signing |
|
| Secrets Management |
|
| Query Management |
|
Known Issues and Caveats
| Issue | Description |
|---|---|
| Removing a custom role | Resolved: Custom roles can now be deleted. See Deleting a Custom User Role. Previously, it was not possible to remove a custom role. |
| Role changes lag time | There may be a lag of up to 30 minutes between making organizational preference changes in the admin console and being able to see them reflected. |
| Edit / Add Organization | A user might be listed multiple times if they are assigned multiple roles within the same organization. |
| Use of basic auth for API calls breaks | Using basic auth for API calls will break and you will be required to use an API Key or JWT. |
| Removing a user from their last assigned role | It is possible to remove a user from all roles. The user is then directed to a notification page alerting them to this. They will then need to contact their administrator. |